In today’s digital era, phone scams are rising, emphasizing the need for heightened vigilance. A recent case involving T-Mobile users underscores the critical importance of awareness in averting fraudulent activities. You can Protect Yourself from T-Mobile iPhone Scams by following the methods below. This narrative recounts the experience of a T-Mobile subscriber who narrowly avoided a complex scam, shedding light on key strategies to detect and prevent such schemes. By sharing this account, individuals can gain valuable insights into the deceptive tactics employed by scammers and empower themselves to safeguard against potential threats. Maintaining awareness of common scam tactics and exercising caution in communications are essential in mitigating the risk of falling victim to fraudulent schemes targeting mobile users.
About T-Mobile iPhone Scams
Multiple Incessant Calls
The ordeal began with persistent calls from a purported T-Mobile number, which immediately raised suspicion due to their unusual frequency and timing.
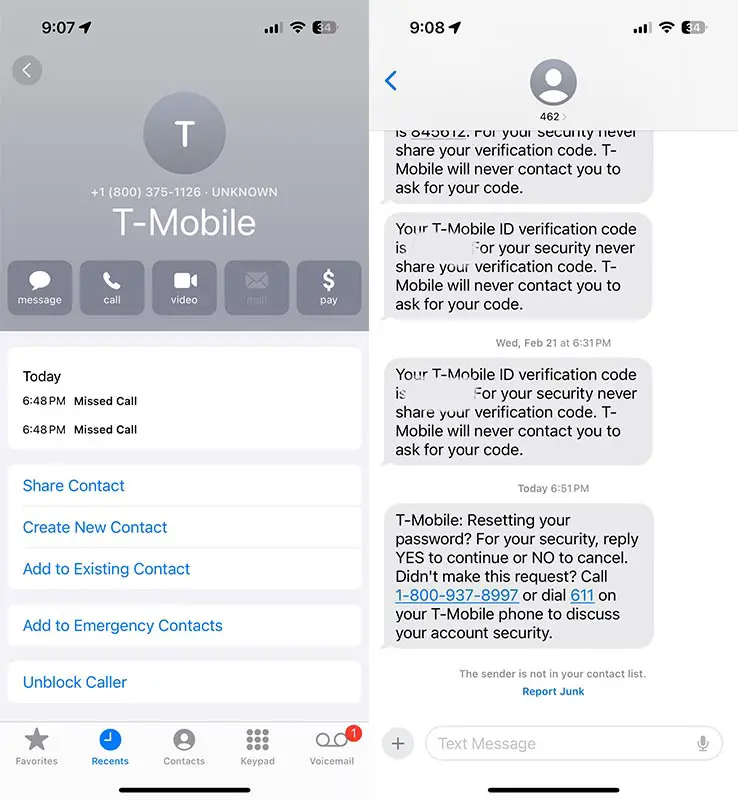
Unverified Transactions
Upon answering the call, the subscriber was informed that unauthorized purchases of high-value iPhones had been made on their account, a claim unsupported by any prior notification or confirmation.
Unusual Billing Address Change
Further skepticism arose when the caller disclosed a sudden alteration in the billing address, a dubious tactic often employed in fraudulent transactions.
The Deceptive Conversation: Unraveling the Scam
False Pretenses of Helpfulness
Despite initial skepticism, the scammer adopted a guise of assistance, offering to cancel the fictitious order and impose a security freeze on the account, luring the victim into a false sense of security.
Insistence on Password Reset
Subsequently, the scammer coerced the victim into resetting their account password under the pretext of enhancing security measures, a ploy to gain unauthorized access to sensitive information.
Text Message Manipulation
Employing deceptive tactics, the scammer orchestrated a text message exchange, soliciting verification codes under the guise of account verification, exploiting the victim’s trust and vulnerability.
Maintaining Alertness: Crucial Steps to Take
Trust Your Gut Instincts
In uncertain situations, trust intuition and caution as crucial defenses against scams. Scrutinize unfamiliar requests and communications for safety.
Prioritize Account Security
Prioritizing safeguarding personal information and assets requires proactive steps like updating passwords regularly and monitoring account activity for anomalies.
Verify with Official Channels
Confirm with official sources, such as contacting the service provider through verified channels for authentication in suspected fraud or phishing attempts.
Parting Advice: Words of Caution
Stay Vigilant Against Spoofing
The prevalence of caller ID spoofing emphasizes skepticism toward incoming calls, especially those claiming to be from reputable sources, which requires discernment and verification.
Exercise Caution with Verification Codes
Verification codes are crucial security measures. Exercise caution to prevent unauthorized access, especially in suspicious contexts, when asked for codes.
Report Suspected Scams Immediately
Swiftly report suspected fraud to authorities or service providers to intervene and mitigate risks, contributing to combatting scams and protecting consumers.
FAQs
How common are phone scams targeting T-Mobile users?
Phone scams targeting T-Mobile users are increasingly prevalent, with scammers employing various tactics to deceive unsuspecting individuals.
What steps can I take to protect myself from phone scams?
To safeguard against phone scams, it’s crucial to remain vigilant, avoid sharing personal information over the phone, and verify the authenticity of calls or messages from purported service providers.
What should I do if I suspect fraudulent activity on my account?
If you suspect fraud, contact the service provider, report it to authorities, and enhance security with measures like password changes.
Are there any warning signs to watch out for in potential scam calls?
Warning signs of scam calls include unsolicited requests for personal information, high-pressure tactics, and inconsistencies in caller information or communication.
How can I contribute to raising awareness about phone scams?
Raising awareness about phone scams includes sharing experiences, reporting suspicious activity, and educating others to protect against fraudulent schemes.
Wrap Up
The T-Mobile subscriber’s story underscores the vital need for vigilance and astute judgment in navigating the digital landscape. To prevent security breaches, individuals must stay vigilant, prioritize securing accounts, and use caution when interacting with unfamiliar entities. Being vigilant and proactive helps individuals build strong defenses against deceptive actors, protecting themselves from financial harm and preserving well-being.
The narrative urges heightened awareness, prompting proactive measures in digital interactions with a discerning and skeptical mindset for individuals. Through vigilance, informed decisions, and prioritizing security, individuals confidently navigate the digital landscape, safeguarding against fraud and deception.

Selva Ganesh is a Computer Science Engineer, Android Developer, and Tech Enthusiast. As the Chief Editor of this blog, he brings over 10 years of experience in Android development and professional blogging. He has completed multiple courses under the Google News Initiative, enhancing his expertise in digital journalism and content accuracy. Selva also manages Android Infotech, a globally recognized platform known for its practical, solution-focused articles that help users resolve Android-related issues.





Leave a Reply